-

Pros and cons of online vs. in-person math tutoring
In the sprawling metropolis of Los Angeles, parents and students have a plethora of educational resources at their fingertips, especially when it comes to math tutoring. However, the abundance of choices often leads to a…
-

Telecom Revolution 2024: Three technologies expected in the future
The telecommunications (telecom) industry worldwide is searching for development opportunities as technology advances, communication needs grow, and demand extends the present barriers. However, the telecom sector is witnessing new challenges with other well-rooted industries, such…
-

What Will Happen if the Mutual Fund SIP Date Falls on a Saturday, Sunday, or on Any Holidays?
Mutual Fund SIP (Systematic Investment Plan) will be triggered for investments on the SIP dates specified by the customers. But in case of a holiday, the same will be triggered on the next immediate following…
-

The rise of the global digital economy: How can you expand your ecommerce business in Europe?
Although it is a small continent geographically, Europe is one of the most powerful centers worldwide. In the past, Europe was renowned mainly for its strong manufacturing industries, such as electronics and automotive, among others,…
-
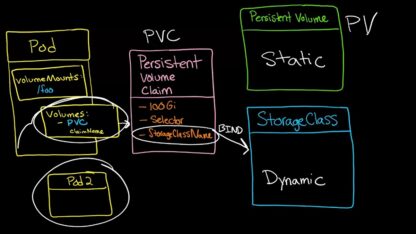
The benefits of using kubernetes persistent volumes in your applications
A persistent volume (PV) is a storage device mounted into Pods. When the Pod is deleted, the content remains on the PV. A PersistentVolumeClaim requests a storage resource that your deployment can claim. It specifies…
-

Here’s the secret to buying a used car
There are plenty of advantages to buying a used car instead of paying top dollar for a new one, but a tight market could make finding the right one challenging. There are a number of…
-

Is 100 Mbps Fast? What Can We Do With It?
In this digital age, internet speed has become a crucial aspect of our daily lives. Connection speeds determine how efficiently we work, communicate, and consume media. Speed has become necessity because we don’t only consume…
-

How to declutter and organize your garage
The garage is an important part of your home. It can hold vehicles, recreational equipment, and lawnmowers with plenty of room for tools and other equipment. Unfortunately, garages often become dumping grounds for forgotten items.…
-

Embracing the Zero Trust Framework
The “Zero Trust Framework” follows a “never trust, always verify” approach to security by insisting that every user and device connecting to network resources must be verified. This framework leverages advanced technologies like risk-based multi-factor…
-

Is It Better to Fast Charge or Slow Charge My Smartphone?
In today’s fast-paced world, our smartphones have become an essential part of our lives. We rely on them for all sorts of communication, entertainment, and staying connected with friends. But when it comes to charging…
-

REITs are safe, but with some risks!
Real Estate Investment Trusts (REITs) are comparatively safe investments, despite bearing inherent risks. These include economic risks leading to fluctuating prices and value decline, increased borrowing cost from higher interest rates, real estate market fluctuations…
-

International faxing for businesses: A complete guide
Faxing has been a cornerstone of business communication for decades. Originating from the era of telegraphs, it evolved into the modern fax machine in the 1960s, offering businesses a dependable means of transmitting vital documents…